Table of Contents
- 1 Introduction
- 2 An Introduction Ansible
- 3 Ansible practice: how to create a user and grant them sudo permissions in Ansible.
- 4 How to disable SELinux in Ansible.
- 5 How to allow ports 22, 80, and 443 in the firewall on Ubuntu using Ansible
- 6 How to change the hostname on Ubuntu, CentOS, RHEL, and Oracle Linux using Ansible.
- 7 5. To list all the packages installed on a target server
- 8 Conclusion
Introduction
Welcome to our comprehensive guide on Ansible practice exercises, where we delve into hands-on examples to master this powerful automation tool. In this tutorial, We will use Ansible practice exercises examples.
An Introduction Ansible
Ansible is a popular open-source automation tool for IT operations and configuration management. One of the key features of Ansible is its ability to execute tasks with elevated privileges, which is often necessary when configuring or managing systems.
Ansible practice: how to create a user and grant them sudo permissions in Ansible.
- name: Create user
user:
name: huupv
state: present
- name: Add user to sudoers
lineinfile:
path: /etc/sudoers
line: "huupv ALL=(ALL) NOPASSWD: ALL"
state: presentIn the first task, the “user” module is used to create a user with the name “huupv”. The “state” directive is set to “present” to ensure that the user is created if it doesn’t already exist.
In the second task, the “lineinfile” module is used to add the user “huupv” to the sudoers file. The “line” directive specifies that “huupv” can run all commands as any user without a password. The “state” directive is set to “present” to ensure that the line is added if it doesn’t already exist in the sudoers file.
Note: It is recommended to use the “visudo” command to edit the sudoers file instead of directly editing the file, as it checks the syntax of the file before saving changes.
You try it ansible!
How to disable SELinux in Ansible.
- name: Disable SELinux
lineinfile:
path: /etc/selinux/config
line: SELINUX=disabled
state: present
- name: Restart the system to apply the changes
command: shutdown -r now
when: "'disabled' in selinux.getenforce()"In the first task, the “lineinfile” module is used to set the SELinux state to “disabled” in the SELinux configuration file located at “/etc/selinux/config”. The “state” directive is set to “present” to ensure that the line is added if it doesn’t already exist in the configuration file.
In the second task, the “command” module is used to restart the system to apply the changes. The “when” directive is used to only execute the task if the SELinux state is currently set to “disabled”.
Note: Disabling SELinux is not recommended for security reasons. If you need to modify the SELinux policy, it is better to set SELinux to “permissive” mode, which logs SELinux violations but does not enforce them, rather than completely disabling SELinux.
How to allow ports 22, 80, and 443 in the firewall on Ubuntu using Ansible
- name: Allow ports 22, 80, and 443 in firewall
ufw:
rule: allow
port: [22,80,443]
- name: Verify firewall rules
command: ufw status
register: firewall_status
- name: Display firewall status
debug:
var: firewall_status.stdout_lines- In the first task, the “ufw” module is used to allow incoming traffic on ports 22, 80, and 443. The “rule” directive is set to “allow” and the “port” directive is set to a list of ports to allow.
- In the second task, the “command” module is used to run the “ufw status” command and register the result in the “firewall_status” variable.
- In the third task, the “debug” module is used to display the firewall status, which is stored in the “firewall_status.stdout_lines” variable.
Note: Make sure the “ufw” firewall is installed and enabled on the target system before running this playbook.
How to change the hostname on Ubuntu, CentOS, RHEL, and Oracle Linux using Ansible.
- name: Change hostname
become: yes
become_method: sudo
lineinfile:
dest: /etc/hosts
regexp: '^.*{{ inventory_hostname }}.*$'
line: '{{ ansible_default_ipv4.address }} {{ new_hostname }} {{ inventory_hostname }}'
state: present
replace:
dest: /etc/hostname
regexp: '^.*{{ inventory_hostname }}.*$'
replace: '{{ new_hostname }}'
state: present
- name: Reload hostname
shell: |
hostname {{ new_hostname }}
echo {{ new_hostname }} > /etc/hostname
if [[ $(grep -q {{ new_hostname }} /etc/sysconfig/network) -eq 0 ]]; then
sed -i "s/^HOSTNAME=.*/HOSTNAME={{ new_hostname }}/" /etc/sysconfig/network
fi
if [[ $(grep -q {{ new_hostname }} /etc/sysconfig/network-scripts/ifcfg-* 2> /dev/null) -eq 0 ]]; then
for ifcfg in $(grep -l {{ inventory_hostname }} /etc/sysconfig/network-scripts/ifcfg-*); do
sed -i "s/^HOSTNAME=.*/HOSTNAME={{ new_hostname }}/" $ifcfg
done
fi
when: "'Ubuntu' in ansible_os_family or 'Debian' in ansible_os_family"
- name: Reload hostname
shell: |
hostname {{ new_hostname }}
echo {{ new_hostname }} > /etc/hostname
sed -i "s/^HOSTNAME=.*/HOSTNAME={{ new_hostname }}/" /etc/sysconfig/network
when: "'RedHat' in ansible_os_family or 'CentOS' in ansible_os_family or 'OracleLinux' in ansible_os_family"
- name: Check the hostname
shell: hostname
register: hostname_check
- name: Display the hostname
debug:
var: hostname_check.stdout- In the first task, the “lineinfile” module is used to update the “/etc/hosts” file with the new hostname, which is specified in the “new_hostname” variable. The “state” directive is set to “present” to ensure the line is added to the file if it doesn’t exist. The “replace” module is used to update the “/etc/hostname” file with the new hostname.
- In the second task, the “shell” module is used to reload the hostname on Ubuntu and Debian systems. The “when” directive is used to only execute this task if the target system is an Ubuntu or Debian system.
- In the third task, the “shell” module is used to reload the hostname on Red Hat, CentOS, and Oracle Linux systems. The “when” directive is used to only execute this task if the target system is a Red Hat, CentOS, or Oracle Linux system.
To run the Ansible playbook
- Save the playbook content in a file with a .yml extension, for example, change_hostname.yml
- Run the command
ansible-playbook change_hostname.ymlon the terminal. - Set the value of the
new_hostnamevariable by passing it as an extra-var argument with the command:ansible-playbook change_hostname.yml --extra-vars "new_hostname=newhostname" - Before running the playbook, ensure you have the target server information in your Ansible inventory file and that the necessary SSH connection is set up.
- If you have set
become: yesin the playbook, make sure you have the necessary permissions on the target server to run the playbook with elevated privileges.
5. To list all the packages installed on a target server
- name: List all packages
hosts: target
tasks:
- name: Get list of all packages
command: "{{ 'dpkg-query -f \'{{.Package}}\\n\' -W' if (ansible_distribution == 'Ubuntu') else 'rpm -qa' }}"
register: packages
- name: Display packages
debug:
var: packages
- Where
targetis the group of hosts defined in the inventory file.
To run this playbook, you can use the following command:
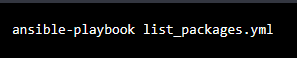
- Where
list_packages.ymlis the name of the playbook file. - This playbook will use the appropriate command (
dpkg-queryfor Ubuntu,rpm -qafor CentOS, RHEL, and Oracle Linux) to get a list of all the installed packages and display them using thedebugmodule.
Note: The ansible_distribution the variable is used to determine the type of operating system running on the target host, and the appropriate command is executed based on the result.
Conclusion
We hope this guide on Ansible practice exercises has empowered you with the knowledge and skills to optimize your IT operations. By walking through these practical examples, you should now feel more confident in using Ansible Automation exercises complex tasks and improve efficiency across your systems. Continue to explore and experiment with Ansible to unlock its full potential and adapt its capabilities to meet your unique operational needs. Update later! Ansible practice exercises examples. I hope will this your helpful. Thank you for reading the DevopsRoles page!
