Table of Contents
Introduction
In this tutorial, How to use NMAP Security Scanner on Linux. How to scan port, service name, and ping v.v to target.
The nmap command is a powerful network scanning tool used for discovering hosts and services on a computer network. It provides a wide range of options and functionalities.
Here are some common use cases of the nmap command:
Install Nmap
CentOS
$ sudo yum install nmap.
Debian
$ sudo apt-get install nmap.
Ubuntu
$ sudo apt-get install nmap.
Syntax use nmap command
nmap [Scan Type] [Options] {Target}
Target
For example, Domain: www.huuphan.com, www.devopsroles.com. IP Address: 192.168.1.4, 10.0.0-255.1-254
Scan Type
-sL: List Scan -- simply list targets to scan -sn: Ping Scan -- disable port scan -sP: Ping Scan -- go no further than determining if host is online -sS/sT/sA/sW/sM: TCP SYN/Connect()/ACK/ Window/Maimon scans -sV: Probe open ports to determine service/version info -sU: UDP Scan -sO: IP protocol scan -- ICMP,EIGRP, -b: FTP bounce scan -n/-R: Never do DNS resolution/Always resolve[default: sometimes]
Options
-p: Only scan specified ports -O: Enable OS detection -P0: Treat all hosts as online -- skip host discovery -e: Use specified interface
nmap command examples
Scan port
# all ports
$ nmap -v -PO www.huuphan.com
# speified port only
$ nmap -v -PO -p 22 192.168.1.0/24
# post scan & service name
$ nmap -v -sV 192.168.1.110ping scan
$ nmap -v -sn 192.168.1.0/24Check the OS of the specified IP
$ nmap -A 192.168.1.110The nmap option –traceroute to trace the route from the scanning machine to the target host
$ nmap -Pn --traceroute -p 443 www.huuphan.comScan multiple hosts:
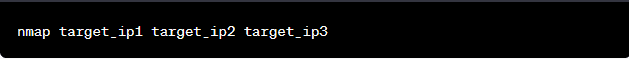
Specify multiple target IP addresses or hostnames separated by spaces.
Conclusion
Nmap command is a simple command in Linux. These are just a few examples of using the nmap command. It’s important to note that scanning hosts or networks without proper authorization may be illegal or against the terms of service.
Make sure you have the necessary permissions and comply with applicable laws and regulations before using nmap. It is a tips and tricks for troubleshooting Linux. Thank you for reading the DevopsRoles page!

