In this tutorial, How to install Metrics Server and install Dashboard Kubernetes.
Table of Contents
Install Metrics Server
Metrics Server is a scalable, efficient source of container resource metrics for Kubernetes built-in autoscaling pipelines.
Prerequisites
You have created an Amazon EKS cluster. By following the steps.
Install Metrics server
kubectl apply -f https://github.com/kubernetes-sigs/metrics-server/releases/download/v0.3.6/components.yaml
#The output
E:\Study\cka\devopsroles> kubectl apply -f https://github.com/kubernetes-sigs/metrics-server/releases/download/v0.3.6/components.yaml
clusterrole.rbac.authorization.k8s.io/system:aggregated-metrics-reader created
clusterrolebinding.rbac.authorization.k8s.io/metrics-server:system:auth-delegator created
rolebinding.rbac.authorization.k8s.io/metrics-server-auth-reader created
apiservice.apiregistration.k8s.io/v1beta1.metrics.k8s.io created
serviceaccount/metrics-server created
deployment.apps/metrics-server created
service/metrics-server created
clusterrole.rbac.authorization.k8s.io/system:metrics-server created
clusterrolebinding.rbac.authorization.k8s.io/system:metrics-server createdCheck metrics-server have deployment
kubectl get deployment metrics-server -n kube-systemThe output terminal
E:\Study\cka\devopsroles>kubectl get deployment metrics-server -n kube-system
NAME READY UP-TO-DATE AVAILABLE AGE
metrics-server 1/1 1 1 19sInstall Dashboard Kubernetes
Refer here.
kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/v2.0.0-beta8/aio/deploy/recommended.yamlThe output resources created in kubernetes-dashboard namespace
E:\Study\cka\devopsroles>kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/v2.0.0-beta8/aio/deploy/recommended.yaml
namespace/kubernetes-dashboard created
serviceaccount/kubernetes-dashboard created
service/kubernetes-dashboard created
secret/kubernetes-dashboard-certs created
secret/kubernetes-dashboard-csrf created
secret/kubernetes-dashboard-key-holder created
configmap/kubernetes-dashboard-settings created
role.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrole.rbac.authorization.k8s.io/kubernetes-dashboard created
rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
deployment.apps/kubernetes-dashboard created
service/dashboard-metrics-scraper created
deployment.apps/dashboard-metrics-scraper createdCheck namespace
kubectl get namespace
kubectl get pod,deployment,svc -n kubernetes-dashboardThe output terminal
E:\Study\cka\devopsroles>kubectl get namespace
NAME STATUS AGE
default Active 12m
kube-node-lease Active 12m
kube-public Active 12m
kube-system Active 12m
kubernetes-dashboard Active 73s
E:\Study\cka\devopsroles>kubectl get pod,deployment,svc -n kubernetes-dashboard
NAME READY STATUS RESTARTS AGE
pod/dashboard-metrics-scraper-76585494d8-hbv6t 1/1 Running 0 60s
pod/kubernetes-dashboard-5996555fd8-qhcxz 1/1 Running 0 64s
NAME READY UP-TO-DATE AVAILABLE AGE
deployment.apps/dashboard-metrics-scraper 1/1 1 1 60s
deployment.apps/kubernetes-dashboard 1/1 1 1 64s
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/dashboard-metrics-scraper ClusterIP 10.100.242.231 <none> 8000/TCP 63s
service/kubernetes-dashboard ClusterIP 10.100.135.44 <none> 443/TCP 78sGet token for dashboard
export AWS_PROFILE=devopsroles-demo
kubectl describe secret $(kubectl get secret -n kubernetes-dashboard | grep kubernetes-dashboard-token | awk '{ print $1 }') -n kubernetes-dashboardThe output terminal token
$ kubectl describe secret $(kubectl get secret -n kubernetes-dashboard | grep kubernetes-dashboard-token | awk '{ print $1 }') -n kubernetes-dashboard
Name: kubernetes-dashboard-token-grg5n
Namespace: kubernetes-dashboard
Labels: <none>
Annotations: kubernetes.io/service-account.name: kubernetes-dashboard
kubernetes.io/service-account.uid: 6a5c693b-892c-4564-9a79-20e0995bc012
Type: kubernetes.io/service-account-token
Data
====
token: eyJhbGciOiJSUzI1NiIsImtpZCI6InVXaXBWU1BGWnp2SFRPaV80c1A1azlhYXA0ZkpyUDhkSlF1MTlkOFNHRG8ifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZC10b2tlbi1ncmc1biIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjZhNWM2OTNiLTg5MmMtNDU2NC05YTc5LTIwZTA5OTViYzAxMiIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlcm5ldGVzLWRhc2hib2FyZDprdWJlcm5ldGVzLWRhc2hib2FyZCJ9.XoYdQMM256sBLVc8x0zcsHn7RXSe03EWZKiNhHxwhCOrFQKPjyuKb__Myw0KNZj-C3Jo2PpvdE9-kcYgKYAPaOg3BWmseTw6cbveGzIs3tTrubgGsTNvxK9M_RGnrSxot_Ajul7-pTAHTaqSELM3CvctbrBRl39drEcIBajbzyHhlWHpkaeFPS2YG3Ct6jLhcm4saZgAV6WxJyb3cAyRdOhuSdM2dLRDJ4LhQTy8wPGHiwY7MWUE-ybi--ehaEExXiBFp2sTUVC8RQQSHoDhb8RCqh9aR9q1AwHEKze6T0lZMLH93RCb3IWEie950aOV7auQntJkeOfLKcE86Uzigw
ca.crt: 1025 bytes
namespace: 20 bytesCreate a secure channel from local to API server in Kubernetes cluster
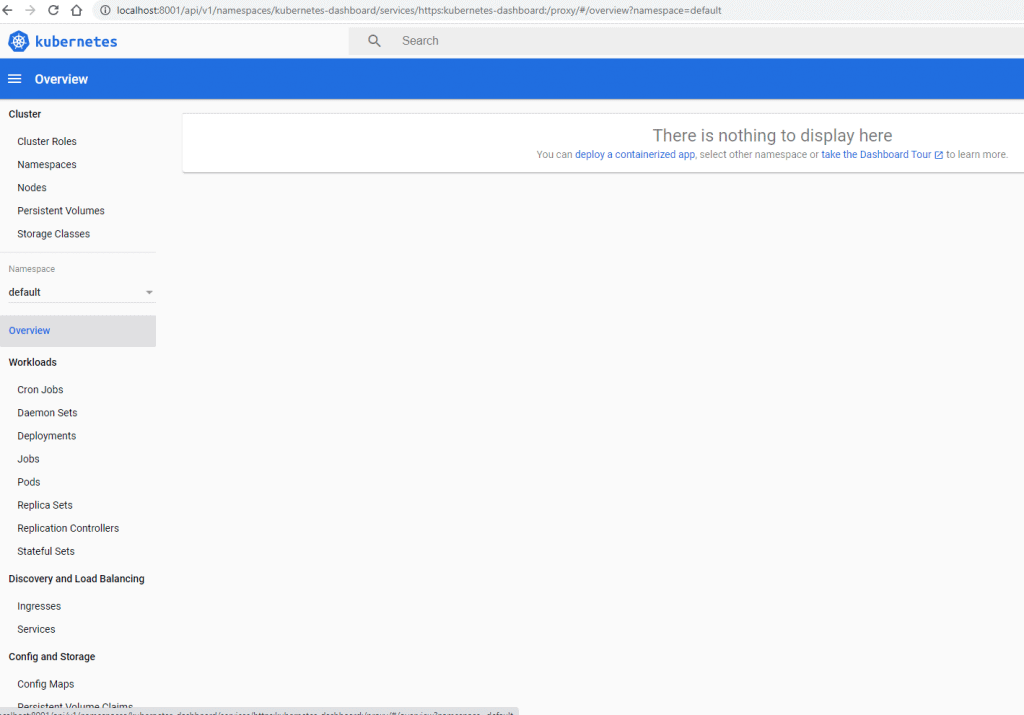
kubectl proxyaccess this url from browser
http://localhost:8001/api/v1/namespaces/kubernetes-dashboard/services/https:kubernetes-dashboard:/proxy/Input token. The result as the picture below
Create RBAC to control what metrics can be visible
File: eks-admin-service-account.yaml with the content as follows
apiVersion: v1
kind: ServiceAccount
metadata:
name: eks-admin
namespace: kube-system
---
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: ClusterRoleBinding
metadata:
name: eks-admin
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin # this is the cluster admin role
subjects:
- kind: ServiceAccount
name: eks-admin
namespace: kube-systemApply it
kubectl apply -f eks-admin-service-account.yamlThe output terminal
E:\Study\cka\devopsroles>kubectl apply -f eks-admin-service-account.yaml
serviceaccount/eks-admin created
clusterrolebinding.rbac.authorization.k8s.io/eks-admin createdCheck it created in kube-system namespace
E:\Study\cka\devopsroles> kubectl get serviceaccount -n kube-system | grep eks-admin
eks-admin 1 67sGet a token from the eks-admin serviceaccount
kubectl -n kube-system describe secret $(kubectl -n kube-system get secret | grep eks-admin | awk '{print $1}')The output terminal token
$ kubectl -n kube-system describe secret $(kubectl -n kube-system get secret | grep eks-admin | awk '{print $1}')
Name: eks-admin-token-k2pxz
Namespace: kube-system
Labels: <none>
Annotations: kubernetes.io/service-account.name: eks-admin
kubernetes.io/service-account.uid: b7005b72-97fc-488b-951d-ac1eaa44dfee
Type: kubernetes.io/service-account-token
Data
====
token: eyJhbGciOiJSUzI1NiIsImtpZCI6InVXaXBWU1BGWnp2SFRPaV80c1A1azlhYXA0ZkpyUDhkSlF1MTlkOFNHRG8ifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJla3MtYWRtaW4tdG9rZW4tazJweHoiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZWtzLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiYjcwMDViNzItOTdmYy00ODhiLTk1MWQtYWMxZWFhNDRkZmVlIiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmVrcy1hZG1pbiJ9.TA-nf-jlyVcUWcvoq7ixMRpZVgsgZ7sBWzTywjMF010bvN4b7p5V5PbMVmNldUylPZ4FQniQY9Xs-quQDytI2TH8zRFdZDFMccEx_E1vzh1CjizKjqbc233N3JYD7xJPTP1U_xq9inaZ3uXvedCtJBzDXVqjjY9eLKcDfuU_I-LLvPEmzh6Sk0FNDzyngAddD_COs2F8q2KbEUOVL6oHr2ZpgbXgxumM_NG_EAKHQx00iXl7Kr_z7wZZSAsvb24ZwQPOShHn_e49C0SvEQKq_TVMG21xxsn0wLIDfH_PpQd1m_vKHbOyyT_yMs_fQnZXnfq_VK7xEhjU3NvdsolMWg
ca.crt: 1025 bytes
namespace: 11 bytesCreate a secure channel from local to API server in Kubernetes cluster
kubectl proxyAccess this URL from browser
http://localhost:8001/api/v1/namespaces/kubernetes-dashboard/services/https:kubernetes-dashboard:/proxy/Input token as the picture below
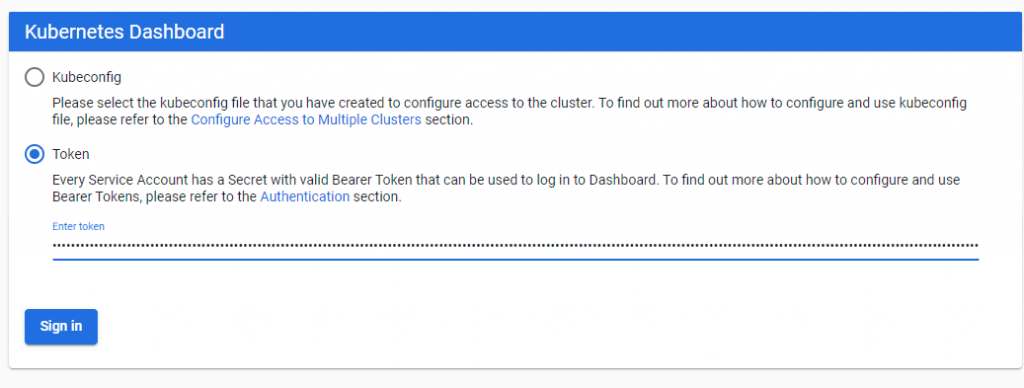
The result have installed k8s dashboard
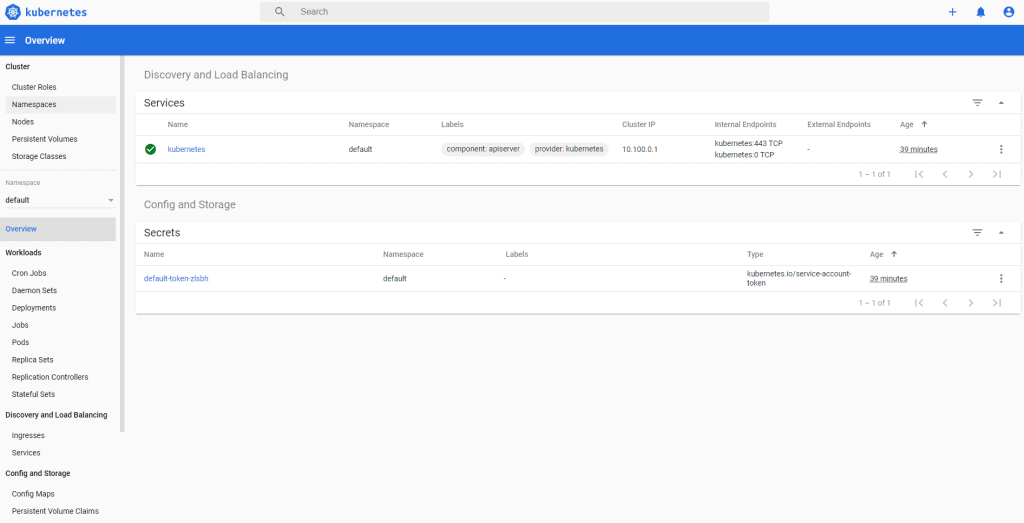
Uninstall Dashboard
kubectl delete -f https://raw.githubusercontent.com/kubernetes/dashboard/v2.0.0-beta8/aio/deploy/recommended.yaml
kubectl delete -f eks-admin-service-account.yamlConclusion
You have to install dashboard Kubernetes. I hope will this your helpful. Thank you for reading the DevopsRoles page!
