Deploying containerized applications on Amazon Elastic Kubernetes Service (EKS) offers incredible scalability and agility. However, this efficiency comes with increased security risks. Malicious code within container images can compromise your entire EKS cluster. One powerful tool to mitigate this risk is the Software Bill of Materials (SBOM). This article delves into the crucial role of SBOM Amazon EKS security, guiding you through the process of identifying vulnerable container images within your EKS environment. We will explore practical techniques and best practices to ensure a robust and secure Kubernetes deployment.
Table of Contents
- 1 Understanding SBOMs and Their Importance in Container Security
- 2 Generating SBOMs for Your Container Images
- 3 Analyzing SBOMs to Find Vulnerable Images on Amazon EKS
- 4 Implementing Secure Container Image Management with SBOM Amazon EKS
- 5 SBOM Amazon EKS: Best Practices for Secure Deployments
- 6 Frequently Asked Questions
- 7 Conclusion
Understanding SBOMs and Their Importance in Container Security
A Software Bill of Materials (SBOM) is a formal record containing a comprehensive list of components, libraries, and dependencies included in a software product. Think of it as a detailed inventory of everything that makes up your container image. For container security, an SBOM provides critical insights into the composition of your images, enabling you to quickly identify potential vulnerabilities before deployment or after unexpected incidents. A well-structured SBOM Amazon EKS analysis allows you to pinpoint components with known security flaws, significantly reducing your attack surface.
The Benefits of Using SBOMs in an EKS Environment
- Improved Vulnerability Detection: SBOMs enable automated vulnerability scanning by comparing the components listed in the SBOM against known vulnerability databases (like the National Vulnerability Database – NVD).
- Enhanced Compliance: Many security and regulatory frameworks require detailed inventory and risk assessment of software components. SBOMs greatly facilitate compliance efforts.
- Supply Chain Security: By understanding the origin and composition of your container images, you can better manage and mitigate risks associated with your software supply chain.
- Faster Remediation: Identifying vulnerable components early in the development lifecycle enables faster remediation, reducing the impact of potential security breaches.
Generating SBOMs for Your Container Images
Several tools can generate SBOMs for your container images. The choice depends on your specific needs and workflow. Here are a few popular options:
Using Syft for SBOM Generation
Syft is an open-source command-line tool that analyzes container images and generates SBOMs in various formats, including SPDX and CycloneDX. It’s lightweight, fast, and easy to integrate into CI/CD pipelines.
# Example using Syft to generate an SPDX SBOM
syft -o spdx-json my-image.tar
Using Anchore Grype for Vulnerability Scanning
Anchore Grype is a powerful vulnerability scanner that leverages SBOMs to identify known security vulnerabilities in container images. It integrates seamlessly with Syft and other SBOM generators.
# Example using Anchore Grype with an SPDX SBOM
grype --sbom my-image.spdx.json
Analyzing SBOMs to Find Vulnerable Images on Amazon EKS
Once you have generated SBOMs for your container images, you need a robust system to analyze them for vulnerabilities. This involves integrating your SBOM generation and analysis tools into your CI/CD pipeline, allowing automated security checks before deployment to your SBOM Amazon EKS cluster.
Integrating SBOM Analysis into your CI/CD Pipeline
Integrating SBOM analysis into your CI/CD pipeline ensures that security checks happen automatically, preventing vulnerable images from reaching your production environment. This often involves using tools like Jenkins, GitLab CI, or GitHub Actions.
- Generate the SBOM: Integrate a tool like Syft into your pipeline to generate an SBOM for each container image built.
- Analyze the SBOM: Use a vulnerability scanner such as Anchore Grype or Trivy to analyze the SBOM and identify known vulnerabilities.
- Fail the build if vulnerabilities are found: Configure your CI/CD pipeline to fail the build if critical or high-severity vulnerabilities are identified.
- Generate reports: Generate comprehensive reports outlining detected vulnerabilities for review and remediation.
Implementing Secure Container Image Management with SBOM Amazon EKS
Effective container image management is paramount for maintaining the security of your SBOM Amazon EKS cluster. This involves implementing robust processes for building, storing, and deploying container images.
Leveraging Container Registries
Utilize secure container registries like Amazon Elastic Container Registry (ECR) or other reputable private registries. These registries provide features such as access control, image scanning, and vulnerability management, significantly enhancing the security posture of your container images.
Implementing Image Scanning and Vulnerability Management
Integrate automated image scanning tools into your workflow to regularly check for vulnerabilities in your container images. Tools such as Clair and Trivy offer powerful scanning capabilities, helping you detect and address vulnerabilities before they become a threat.
Utilizing Immutable Infrastructure
Adopting immutable infrastructure principles helps mitigate risks by ensuring that once a container image is deployed, it’s not modified. This reduces the chance of accidental or malicious changes compromising your EKS cluster’s security.
SBOM Amazon EKS: Best Practices for Secure Deployments
Combining SBOMs with other security best practices ensures a comprehensive approach to protecting your EKS environment.
- Regular Security Audits: Conduct regular security audits to assess your EKS cluster’s security posture and identify potential weaknesses.
- Least Privilege Access Control: Implement strict least-privilege access control policies to limit the permissions granted to users and services within your EKS cluster.
- Network Segmentation: Segment your network to isolate your EKS cluster from other parts of your infrastructure, limiting the impact of potential breaches.
- Regular Updates and Patching: Stay up-to-date with the latest security patches for your Kubernetes control plane, worker nodes, and container images.
Frequently Asked Questions
What is the difference between an SBOM and a vulnerability scan?
An SBOM is a comprehensive inventory of software components in a container image. A vulnerability scan uses the SBOM (or directly analyzes the image) to check for known security vulnerabilities in those components against vulnerability databases. The SBOM provides the “what” (components), while the vulnerability scan provides the “why” (security risks).
How do I choose the right SBOM format?
The choice of SBOM format often depends on the tools you’re using in your workflow. SPDX and CycloneDX are two widely adopted standards offering excellent interoperability. Consider the requirements of your vulnerability scanning tools and compliance needs when making your selection.
Can I use SBOMs for compliance purposes?
Yes, SBOMs are crucial for demonstrating compliance with various security regulations and industry standards, such as those related to software supply chain security. They provide the necessary transparency and traceability of software components, facilitating compliance audits.
What if I don’t find a vulnerability scanner that supports my SBOM format?
Many tools support multiple SBOM formats, or converters are available to translate between formats. If a specific format is not supported, consider using a converter to transform your SBOM to a compatible format before analysis.
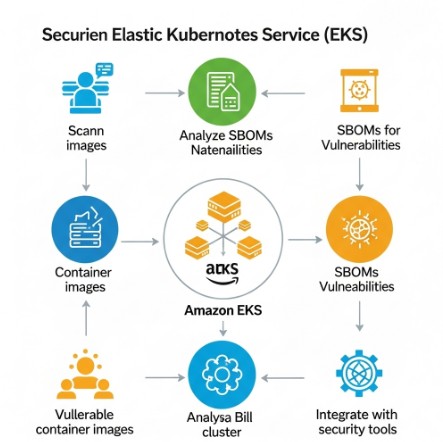
Conclusion
Implementing robust security measures for your Amazon EKS deployments is crucial in today’s threat landscape. By leveraging SBOM Amazon EKS analysis, you gain a powerful tool to identify vulnerable container images proactively, ensuring a secure and reliable containerized application deployment. Remember that integrating SBOM generation and analysis into your CI/CD pipeline is not just a best practice—it’s a necessity for maintaining the integrity of your EKS cluster and protecting your organization’s sensitive data. Don’t underestimate the significance of SBOM Amazon EKS security—make it a core part of your DevOps strategy.
For more information on SBOMs, you can refer to the SPDX standard and CycloneDX standard websites. Further reading on securing container images can be found on the official Amazon ECR documentation. Thank you for reading the DevopsRoles page!

