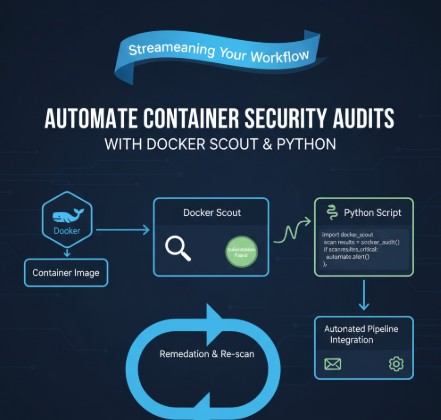
In the modern software development lifecycle, containers have become the de facto standard for packaging and deploying applications. Their portability and consistency offer immense benefits, but they also introduce a complex new layer for security management. As development velocity increases, manually inspecting every container image for vulnerabilities is not just inefficient; it’s impossible. This is where the practice of automated container security audits becomes a critical component of a robust DevSecOps strategy. This article provides a comprehensive, hands-on guide for developers, DevOps engineers, and security professionals on how to leverage the power of Docker Scout and the versatility of Python to build an automated security auditing workflow, ensuring vulnerabilities are caught early and consistently.
Table of Contents
Understanding the Core Components: Docker Scout and Python
Before diving into the automation scripts, it’s essential to understand the two key technologies that form the foundation of our workflow. Docker Scout provides the security intelligence, while Python acts as the automation engine that glues everything together.
What is Docker Scout?
Docker Scout is an advanced software supply chain management tool integrated directly into the Docker ecosystem. Its primary function is to provide deep insights into the contents and security posture of your container images. It goes beyond simple vulnerability scanning by offering a multi-faceted approach to security.
- Vulnerability Scanning: At its core, Docker Scout analyzes your image layers against an extensive database of Common Vulnerabilities and Exposures (CVEs). It provides detailed information on each vulnerability, including its severity (Critical, High, Medium, Low), the affected package, and the version that contains a fix.
- Software Bill of Materials (SBOM): Scout automatically generates a detailed SBOM for your images. An SBOM is a complete inventory of all components, libraries, and dependencies within your software. This is crucial for supply chain security, allowing you to quickly identify if you’re affected by a newly discovered vulnerability in a transitive dependency.
- Policy Evaluation: For teams, Docker Scout offers a powerful policy evaluation engine. You can define rules, such as “fail any build with critical vulnerabilities” or “alert on packages with non-permissive licenses,” and Scout will automatically enforce them.
- Cross-Registry Support: While deeply integrated with Docker Hub, Scout is not limited to it. It can analyze images from various other registries, including Amazon ECR, Artifactory, and even local images on your machine, making it a versatile tool for diverse environments. You can find more details in the official Docker Scout documentation.
Why Use Python for Automation?
Python is the language of choice for DevOps and automation for several compelling reasons. Its simplicity, combined with a powerful standard library and a vast ecosystem of third-party packages, makes it ideal for scripting complex workflows.
- Simplicity and Readability: Python’s clean syntax makes scripts easy to write, read, and maintain, which is vital for collaborative DevOps environments.
- Powerful Standard Library: Modules like
subprocess(for running command-line tools),json(for parsing API and tool outputs), andos(for interacting with the operating system) are included by default. - Rich Ecosystem: Libraries like
requestsfor making HTTP requests to APIs (e.g., posting alerts to Slack or Jira) andpandasfor data analysis make it possible to build sophisticated reporting and integration pipelines. - Platform Independence: Python scripts run consistently across Windows, macOS, and Linux, which is essential for teams using different development environments.
Setting Up Your Environment for Automated Container Security Audits
To begin, you need to configure your local machine to run both Docker Scout and the Python scripts we will develop. This setup process is straightforward and forms the bedrock of our automation.
Prerequisites
Ensure you have the following tools installed and configured on your system:
- Docker Desktop: You need a recent version of Docker Desktop (for Windows, macOS, or Linux). Docker Scout is integrated directly into Docker Desktop and the Docker CLI.
- Python 3.x: Your system should have Python 3.6 or a newer version installed. You can verify this by running
python3 --versionin your terminal. - Docker Account: You need a Docker Hub account. While much of Scout’s local analysis is free, full functionality and organizational features require a subscription.
- Docker CLI Login: You must be authenticated with the Docker CLI. Run
docker loginand enter your credentials.
Enabling Docker Scout
Docker Scout is enabled by default in recent versions of Docker Desktop. You can verify its functionality by running a basic command against a public image:
docker scout cves nginx:latest
This command will fetch the vulnerability data for the latest NGINX image and display it in your terminal. If this works, your environment is ready.
Installing Necessary Python Libraries
For our scripts, we won’t need many external libraries initially, as we’ll rely on Python’s standard library. However, for more advanced reporting, the requests library is invaluable for API integrations.
Install it using pip:
pip install requests
A Practical Guide to Automating Docker Scout with Python
Now, let’s build the Python script to automate our container security audits. We’ll start with a basic script to trigger a scan and parse the results, then progressively add more advanced logic for policy enforcement and reporting.
The Automation Workflow Overview
Our automated process will follow these logical steps:
- Target Identification: The script will accept a container image name and tag as input.
- Scan Execution: It will use Python’s
subprocessmodule to execute thedocker scout cvescommand. - Output Parsing: The command will be configured to output in JSON format, which is easily parsed by Python.
- Policy Analysis: The script will analyze the parsed data against a predefined set of security rules (our “policy”).
- Result Reporting: Based on the analysis, the script will produce a clear pass/fail result and a summary report.
Step 1: Triggering a Scan via Python’s `subprocess` Module
The subprocess module is the key to interacting with command-line tools from within Python. We’ll use it to run Docker Scout and capture its output.
Here is a basic Python script, audit_image.py, to achieve this:
import subprocess
import json
import sys
def run_scout_scan(image_name):
"""
Runs the Docker Scout CVE scan on a given image and returns the JSON output.
"""
if not image_name:
print("Error: Image name not provided.")
return None
command = [
"docker", "scout", "cves", image_name, "--format", "json", "--only-severity", "critical,high"
]
print(f"Running scan on image: {image_name}...")
try:
result = subprocess.run(
command,
capture_output=True,
text=True,
check=True
)
# The JSON output might have multiple JSON objects, we are interested in the vulnerability list
# We find the line that starts with '{"vulnerabilities":'
for line in result.stdout.splitlines():
if '"vulnerabilities"' in line:
return json.loads(line)
return {"vulnerabilities": []} # Return empty list if no vulnerabilities found
except subprocess.CalledProcessError as e:
print(f"Error running Docker Scout: {e}")
print(f"Stderr: {e.stderr}")
return None
except json.JSONDecodeError as e:
print(f"Error parsing JSON output: {e}")
return None
if __name__ == "__main__":
if len(sys.argv) < 2:
print("Usage: python audit_image.py ")
sys.exit(1)
target_image = sys.argv[1]
scan_results = run_scout_scan(target_image)
if scan_results:
print("\nScan complete. Raw JSON output:")
print(json.dumps(scan_results, indent=2))
How to run it:
python audit_image.py python:3.9-slim
Explanation:
- The script takes the image name as a command-line argument.
- It constructs the
docker scout cvescommand. We use--format jsonto get machine-readable output and--only-severity critical,highto focus on the most important threats. subprocess.run()executes the command.capture_output=Truecaptures stdout and stderr, andcheck=Trueraises an exception if the command fails.- The script then parses the JSON output and prints it. The logic specifically looks for the line containing the vulnerability list, as the Scout CLI can sometimes output other status information. For more detailed information on the module, consult the official Python `subprocess` documentation.
Step 2: Implementing a Custom Security Policy
Simply listing vulnerabilities is not enough; we need to make a decision based on them. This is where a security policy comes in. Our policy will define the acceptable risk level.
Let’s define a simple policy: The audit fails if there is one or more CRITICAL vulnerability OR more than five HIGH vulnerabilities.
We’ll add a function to our script to enforce this policy.
# Add this function to audit_image.py
def analyze_results(scan_data, policy):
"""
Analyzes scan results against a defined policy and returns a pass/fail status.
"""
if not scan_data or "vulnerabilities" not in scan_data:
print("No vulnerability data to analyze.")
return "PASS", "No vulnerabilities found or data unavailable."
vulnerabilities = scan_data["vulnerabilities"]
# Count vulnerabilities by severity
severity_counts = {"CRITICAL": 0, "HIGH": 0}
for vuln in vulnerabilities:
severity = vuln.get("severity")
if severity in severity_counts:
severity_counts[severity] += 1
print(f"\nAnalysis Summary:")
print(f"- Critical vulnerabilities found: {severity_counts['CRITICAL']}")
print(f"- High vulnerabilities found: {severity_counts['HIGH']}")
# Check against policy
fail_reasons = []
if severity_counts["CRITICAL"] > policy["max_critical"]:
fail_reasons.append(f"Exceeded max critical vulnerabilities (found {severity_counts['CRITICAL']}, max {policy['max_critical']})")
if severity_counts["HIGH"] > policy["max_high"]:
fail_reasons.append(f"Exceeded max high vulnerabilities (found {severity_counts['HIGH']}, max {policy['max_high']})")
if fail_reasons:
return "FAIL", ". ".join(fail_reasons)
else:
return "PASS", "Image meets the defined security policy."
# Modify the `if __name__ == "__main__":` block
if __name__ == "__main__":
if len(sys.argv) < 2:
print("Usage: python audit_image.py ")
sys.exit(1)
target_image = sys.argv[1]
# Define our security policy
security_policy = {
"max_critical": 0,
"max_high": 5
}
scan_results = run_scout_scan(target_image)
if scan_results:
status, message = analyze_results(scan_results, security_policy)
print(f"\nAudit Result: {status}")
print(f"Details: {message}")
# Exit with a non-zero status code on failure for CI/CD integration
if status == "FAIL":
sys.exit(1)
Now, when you run the script, it will not only list the vulnerabilities but also provide a clear PASS or FAIL verdict. The non-zero exit code on failure is crucial for CI/CD pipelines, as it will cause the build step to fail automatically.
Integrating Automated Audits into Your CI/CD Pipeline
The true power of this automation script is realized when it’s integrated into a CI/CD pipeline. This “shifts security left,” enabling developers to get immediate feedback on the security of the images they build, long before they reach production.
Below is a conceptual example of how to integrate our Python script into a GitHub Actions workflow. This workflow builds a Docker image and then runs our audit script against it.
Example: GitHub Actions Workflow
Create a file named .github/workflows/security_audit.yml in your repository:
name: Docker Image Security Audit
on:
push:
branches: [ "main" ]
pull_request:
branches: [ "main" ]
jobs:
build-and-audit:
runs-on: ubuntu-latest
steps:
- name: Checkout repository
uses: actions/checkout@v3
- name: Set up Docker Buildx
uses: docker/setup-buildx-action@v2
- name: Login to Docker Hub
uses: docker/login-action@v2
with:
username: ${{ secrets.DOCKERHUB_USERNAME }}
password: ${{ secrets.DOCKERHUB_TOKEN }}
- name: Build and push Docker image
id: docker_build
uses: docker/build-push-action@v4
with:
context: .
file: ./Dockerfile
push: true
tags: ${{ secrets.DOCKERHUB_USERNAME }}/myapp:${{ github.sha }}
- name: Setup Python
uses: actions/setup-python@v4
with:
python-version: '3.9'
- name: Run Container Security Audit
run: |
# Assuming your script is in a 'scripts' directory
python scripts/audit_image.py ${{ secrets.DOCKERHUB_USERNAME }}/myapp:${{ github.sha }}
Key aspects of this workflow:
- It triggers on pushes and pull requests to the main branch.
- It logs into Docker Hub using secrets stored in GitHub.
- The
docker/build-push-actionbuilds the image from a Dockerfile and pushes it to a registry. This is necessary for Docker Scout to analyze it effectively in a CI environment. - Finally, it runs our
audit_image.pyscript. If the script exits with a non-zero status code (as we programmed it to do on failure), the entire workflow will fail, preventing the insecure code from being merged. This creates a critical security gate in the development process, aligning with best practices for CI/CD security.
Frequently Asked Questions (FAQ)
Can I use Docker Scout for images that are not on Docker Hub?
Yes. Docker Scout is designed to be registry-agnostic. You can analyze local images on your machine simply by referencing them (e.g., my-local-app:latest). For CI/CD environments and team collaboration, you can connect Docker Scout to other popular registries like Amazon ECR, Google Artifact Registry, and JFrog Artifactory to gain visibility across your entire organization.
Is Docker Scout a free tool?
Docker Scout operates on a freemium model. The free tier, included with a standard Docker account, provides basic vulnerability scanning and SBOM generation for local images and Docker Hub public images. For advanced features like central policy management, integration with multiple private registries, and detailed supply chain insights, a paid Docker Business subscription is required.
What is an SBOM and why is it important for container security?
SBOM stands for Software Bill of Materials. It is a comprehensive, machine-readable inventory of all software components, dependencies, and libraries included in an application or, in this case, a container image. Its importance has grown significantly as software supply chains have become more complex. An SBOM allows organizations to quickly and precisely identify all systems affected by a newly discovered vulnerability in a third-party library, drastically reducing response time and risk exposure.
How does Docker Scout compare to other open-source tools like Trivy or Grype?
Tools like Trivy and Grype are excellent, widely-used open-source vulnerability scanners. Docker Scout’s key differentiators lie in its deep integration with the Docker ecosystem (Docker Desktop, Docker Hub) and its focus on the developer experience. Scout provides remediation advice directly in the developer’s workflow and expands beyond just CVE scanning to offer holistic supply chain management features, including policy enforcement and deeper package metadata analysis, which are often premium features in other platforms.
Conclusion
In a world of continuous delivery and complex software stacks, manual security checks are no longer viable. Automating your container security audits is not just a best practice; it is a necessity for maintaining a strong security posture. By combining the deep analytical power of Docker Scout with the flexible automation capabilities of Python, teams can create a powerful, customized security gate within their CI/CD pipelines. This proactive approach ensures that vulnerabilities are identified and remediated early in the development cycle, reducing risk, minimizing costly fixes down the line, and empowering developers to build more secure applications from the start. The journey into automated container security audits begins with a single script, and the framework outlined here provides a robust foundation for building a comprehensive and effective DevSecOps program.Thank you for reading the DevopsRoles page!
