In a world where containerized applications are the backbone of micro‑service architectures, Docker Security Hardening is no longer optional—it’s essential. As you deploy containers in production, you’re exposed to a range of attack vectors: privilege escalation, image tampering, insecure runtime defaults, and more. This guide walks you through seven battle‑tested hardening techniques that protect your Docker hosts, images, and containers from the most common threats, while keeping your DevOps workflows efficient.
Table of Contents
- 1 Tip 1: Choose Minimal Base Images
- 2 Tip 2: Run Containers as a Non‑Root User
- 3 Tip 3: Use Read‑Only Filesystems
- 4 Tip 4: Limit Capabilities and Disable Privileged Mode
- 5 Tip 5: Enforce Security Profiles – SELinux and AppArmor
- 6 Tip 6: Use Docker Secrets and Avoid Environment Variables for Sensitive Data
- 7 Tip 7: Keep Images Updated and Scan for Vulnerabilities
- 8 Frequently Asked Questions
- 9 Conclusion
Tip 1: Choose Minimal Base Images
Every extra layer in your image is a potential attack surface. By selecting a slim, purpose‑built base—such as alpine, distroless, or a minimal debian variant—you reduce the number of packages, libraries, and compiled binaries that attackers can exploit. Minimal images also shrink your image size, improving deployment times.
- Use
--platformto lock the OS architecture. - Remove build tools after compilation. For example, install
gccjust for the build step, then delete it in the final image. - Leverage multi‑stage builds. This technique allows you to compile from a full Debian image but copy only the artifacts into a lightweight runtime image.
# Dockerfile example: multi‑stage build
FROM golang:1.22 AS builder
WORKDIR /app
COPY . .
RUN go build -o myapp .
FROM alpine:3.20
WORKDIR /app
COPY --from=builder /app/myapp .
CMD ["./myapp"]
Tip 2: Run Containers as a Non‑Root User
Containers default to the root user, which grants full host access if the container is compromised. Creating a dedicated user in the image and using the --user flag mitigates this risk. Docker also supports USER directives in the Dockerfile to enforce this at build time.
# Dockerfile snippet
RUN addgroup -S appgroup && adduser -S appuser -G appgroup
USER appuser
When running the container, you can double‑check the user with:
docker run --rm myimage id
Tip 3: Use Read‑Only Filesystems
Mount the container’s filesystem as read‑only to prevent accidental or malicious modifications. If your application needs to write logs or temporary data, mount dedicated writable volumes. This practice limits the impact of a compromised container and protects the integrity of your image.
docker run --read-only --mount type=tmpfs,destination=/tmp myimage
Tip 4: Limit Capabilities and Disable Privileged Mode
Docker grants all Linux capabilities by default, many of which are unnecessary for most services. Use the --cap-drop flag to remove them, and drop the dangerous SYS_ADMIN capability unless explicitly required.
docker run --cap-drop ALL --cap-add NET_BIND_SERVICE myimage
Privileged mode should be a last resort. If you must enable it, isolate the container in its own network namespace and use user namespaces for added isolation.
Tip 5: Enforce Security Profiles – SELinux and AppArmor
Linux security modules like SELinux and AppArmor add mandatory access control (MAC) that further restricts container actions. Enabling them on the Docker host and binding a profile to your container strengthens the barrier between the host and the container.
- SELinux: Use
--security-opt label=type:my_label_twhen running containers. - AppArmor: Apply a custom profile via
--security-opt apparmor=myprofile.
For detailed guidance, consult the Docker documentation on Seccomp and AppArmor integration.
Tip 6: Use Docker Secrets and Avoid Environment Variables for Sensitive Data
Storing secrets in environment variables or plain text files is risky because they can leak via container logs or process listings. Docker Secrets, managed through Docker Swarm or orchestrators like Kubernetes, keep secrets encrypted at rest and provide runtime injection.
# Create a secret
echo "my-super-secret" | docker secret create my_secret -
# Deploy service with the secret
docker service create --name myapp --secret my_secret myimage
If you’re not using Swarm, consider external secret managers such as HashiCorp Vault or AWS Secrets Manager.
Tip 7: Keep Images Updated and Scan for Vulnerabilities
Image drift and outdated dependencies can expose known CVEs. Automate image updates using tools like Anchore Engine or Docker’s own image scanning feature. Sign your images with Docker Content Trust to ensure provenance and integrity.
# Enable Docker Content Trust
export DOCKER_CONTENT_TRUST=1
# Sign image
docker trust sign myimage:latest
Run docker scan during CI to catch vulnerabilities early:
docker scan myimage:latest
Frequently Asked Questions
What is the difference between Docker Security Hardening and general container security?
Docker Security Hardening focuses on the specific configuration options, best practices, and tooling available within the Docker ecosystem—such as Dockerfile directives, runtime flags, and Docker’s built‑in scanning—while general container security covers cross‑platform concerns that apply to any OCI‑compatible runtime.
Do I need to re‑build images after applying hardening changes?
Any change that affects the container’s runtime behavior (like adding USER or --cap-drop) requires a new image layer. It’s good practice to rebuild and re‑tag the image to preserve a clean history.
Can I trust --read-only to fully secure my container?
It significantly reduces modification risks, but it’s not a silver bullet. Combine it with other hardening techniques, and never rely on a single configuration to protect your entire stack.
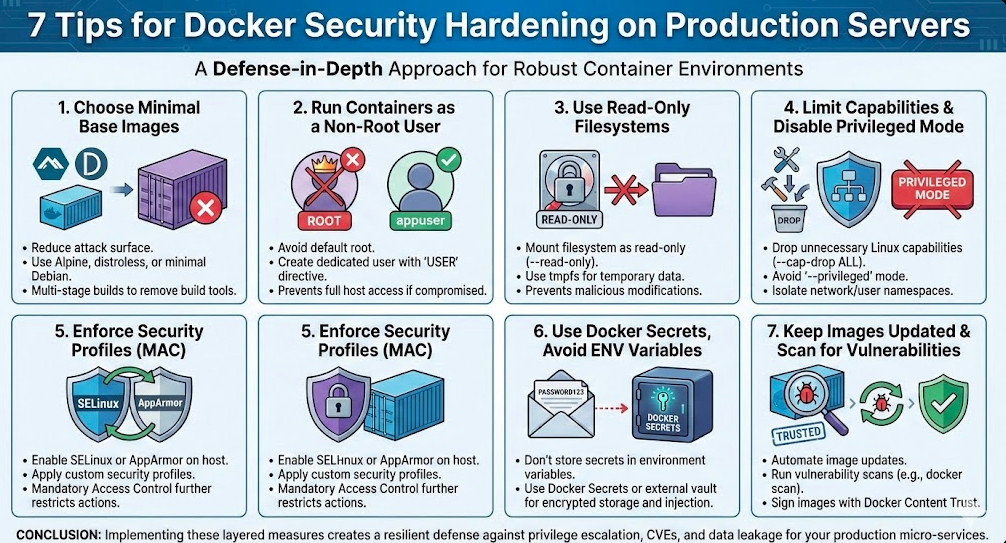
Conclusion
Implementing these seven hardening measures is the cornerstone of a robust Docker production environment. Minimal base images, non‑root users, read‑only filesystems, limited capabilities, enforced MAC profiles, secret management, and continuous image updates together create a layered defense strategy that defends against privilege escalation, CVE exploitation, and data leakage. By routinely auditing your Docker host and container configurations, you’ll ensure that Docker Security Hardening remains an ongoing commitment, keeping your micro‑services resilient, compliant, and ready for any future threat. Thank you for reading the DevopsRoles page!
